The Bluehat Platform
Discover the power that Cyber Threat Detection Bounty Programs bring to your security posture
A new and innovative approach to threat detection
Despite billions of dollars spent across the industry, organisations are faced with
The traditional approach to threat detection is broken.
Security experts are faced with an overwhelming amount of threats, systems, log types and threat detection rules to manage.
In addition to this limitations on technology, resources and budgets reduce threat detection capabilities. As a result, threats are being missed and organisations across the board are at risk.
Through the Bluehat platform
The Bluehat Platform:
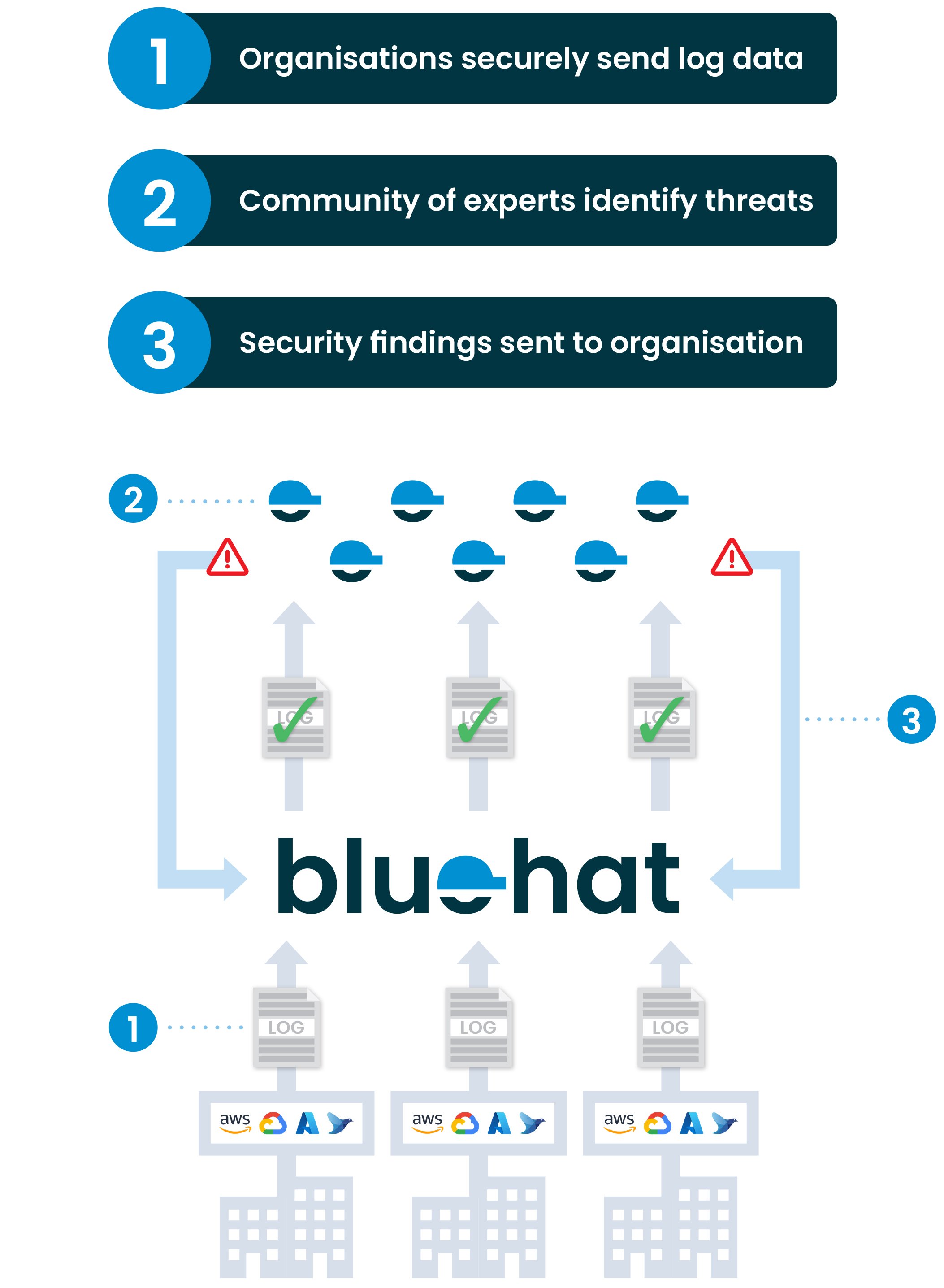
How it works
Bluehat Platform Functionality
Safely preparing your log data
Measurable Threat Coverage
Tailored threat detection coverage to support your organisation’s unique needs.
Company benefits
Save money
Pay for results, only when threats are detected.
Expand coverage
Access to a trusted community of threat detection specialists.
Maintain control
You decide who accesses your data
Reduce complexity
Securely forward log data. That’s it.
Analyst benefits
Be rewarded for your expertise
Focus on your expertise and passion as a threat detection specialist.
Work on your terms
Part-time, full-time or anytime.
Solution your way
Use the tools and platforms you know and love.
Help organisations worldwide
Increase your reputation and income while making an impact. Let’s raise the bar for all.