The Bluehat Platform
The next generation of Detection & Response bringing the power of the combined industries experts to protecting your organisation
The traditional approach to Detection & Response
Does not scale
Despite billions of dollars spent across the security industry, we are faced with
Building and keeping your security team’s skills long-term is challenging. Once your junior staff become skilled, they often leave for higher pay elsewhere.
Customers and the security industry both vie for the same scarce talent pool.
Security experts deal with many threats, systems, logs, and rules. It's too much for even big Security Operation Center teams.
Trying to handle all threats alone causes stress, burnout, and fear of missed incidents.
SIEM costs and setup affect threat detection and response efficiency. Limited log data and processing power hinder real-time monitoring and forensic response.
Infrastructure upkeep poses challenges for organisations and security providers.
Achieve Detection & Response that scales
People
Powered by the collective industry of threat detection & response experts!
With hundreds of security experts (and growing daily) bringing their smarts to bear you gain the broadest and deepest threat coverage possible.
Process
Our approach rewards the efforts of threat research and development!
Focussing on specific TTPs, threat actor groups and current events allows for what is normally not feasible in a traditional approach to delivering detection & response capabilities.
Technology
An approach that is hyper focussd on enabling threat detection & response
We scale with you and enable the community of experts to do what they do best with the technology that they are best at using.
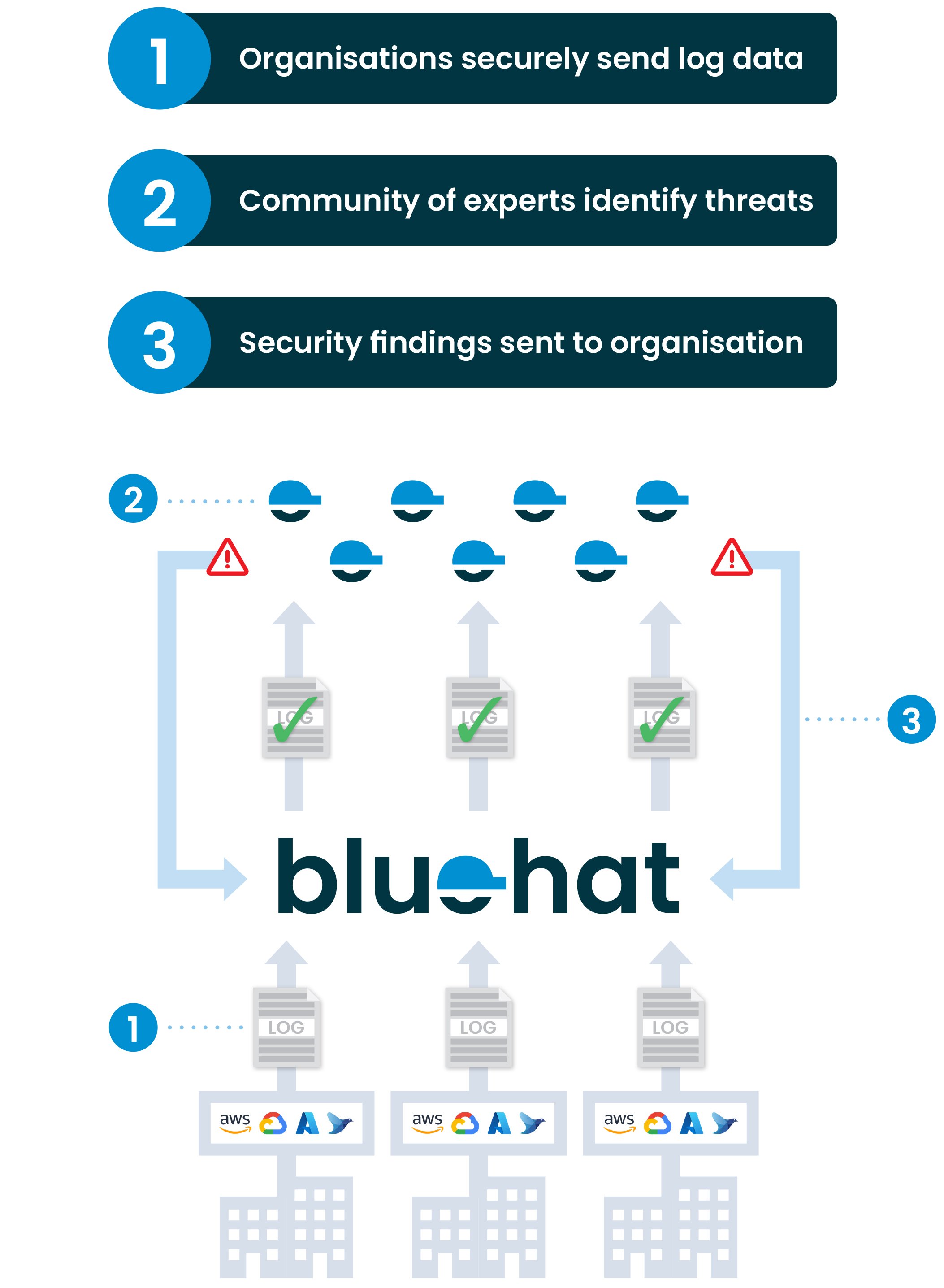
How it works
(It is pretty simple)
Bluehat Platform Functionality
Security is in our DNA
We understand the importance of your data and the trust your customers place in you.
We employ controls across all security domains to ensure your data is secure in transit, usage and rest.
Securing your log data
Others stop at infrastructure security.
We secure your actual log data itself for trusted detection & response actions.
Measurable Threat Coverage
Tailored threat detection coverage to support your organisation’s unique needs.